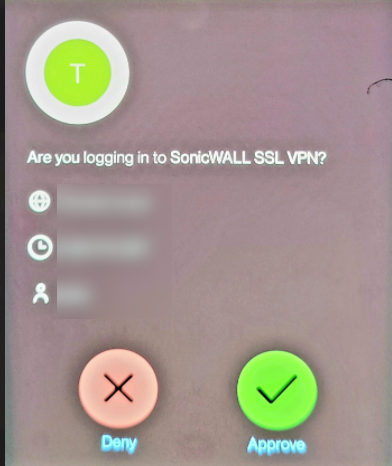
Today we’re going to setup DUO Authentication for the SonicWALL SSL, this will allow users to use 2FA when connecting to the VPN. When they are prompted, it’ll look like the image below. Before you proceed, make sure you have the SSL VPN setup, you can set that up using the SonicWALL guide found below
https://www.sonicwall.com/support/knowledge-base/how-can-i-setup-ssl-vpn/170505609285133/
Duo Admin Portal Setup
- Log into the DUO Admin Portal and select the desired customer, you can find the link for the Admin Portal here https://admin.duosecurity.com/login?next=%2F
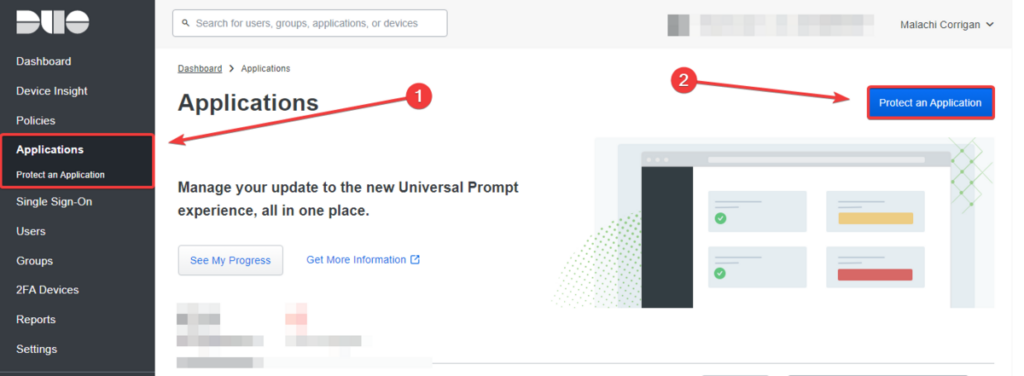
- Select Applications on the left hand side and click Protect an Application
- Search for Radius and click Protect

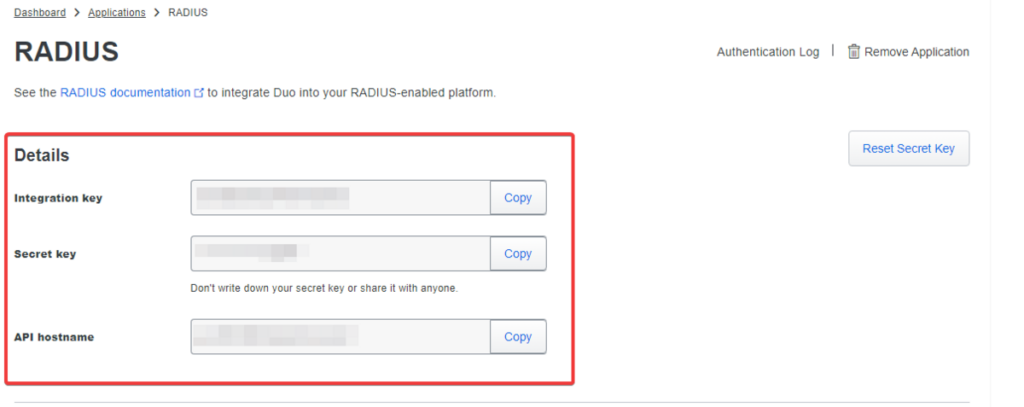
- Note down the Integration key, Secret Key, and API hostname for later use
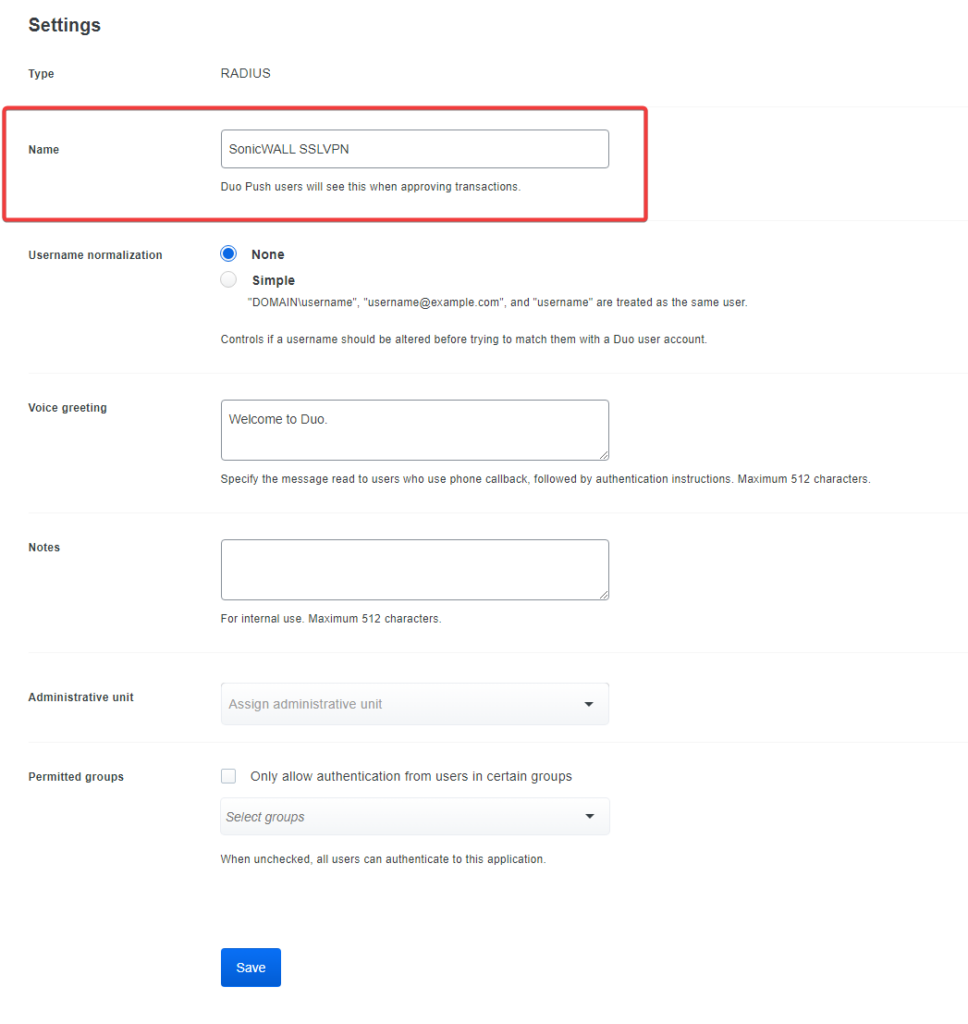
- Name the Application SonicWALL SSLVPN, and adjust name normalization if needed. You can reference this KB if needed
https://help.duo.com/s/article/3261?language=en_US#:~:text=The%20%22Username%20normalization%22%20option%20controls,to%20a%20Duo%20user%20account
DUO Authentication Proxy Setup
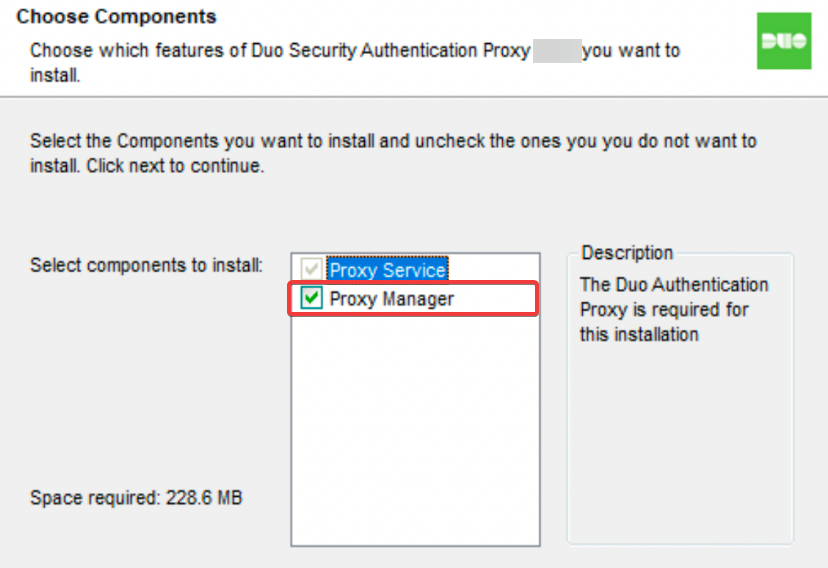
- Install the Duo Authentication Proxy on a server, DUO recommends not installing this on a domain controller due to potential conflicts with ports. When installing make sure to check the Proxy Manager
https://dl.duosecurity.com/duoauthproxy-latest.exe
- Within the Proxy Manager, edit the authproxy.cfg with the code below. Reference the KB below if you need more information
https://duo.com/docs/authproxy-reference[ad_client] host=SERVERNAME host_2=SERVERNAME2 (THIS LINE IS OPTIONAL) service_account_username=LDAP SERVICE ACCOUNT USERNAME service_account_password=LDAP SERVICE ACCOUNT PASSWORD search_dn=DISTINGUISHED NAME OF AD DOMAIN security_group_dn=VPN GROUP DISTINGUISHED NAME [radius_server_auto] ikey=INTEGRATION KEY FROM DUO ADMIN PORTAL skey=SECRET KEY FROM DUO ADMIN PORTAL api_host=API HOSTNAME FROM DUO ADMIN PORTAL radius_ip_1=SONICWALL FIREWALL IP ADDRESS radius_secret_1=RADIUS SECRET KEY FOR LATER USE ON SONICWALL failmode=CAN EITHER BE SAFE OR SECURE (SAFE MEANS FAIL OPEN, SECURE MEANS FAIL CLOSE WHERE PRIMARY AUTHENTICATION IS SUCCESSFUL) client=ad_client port=1812
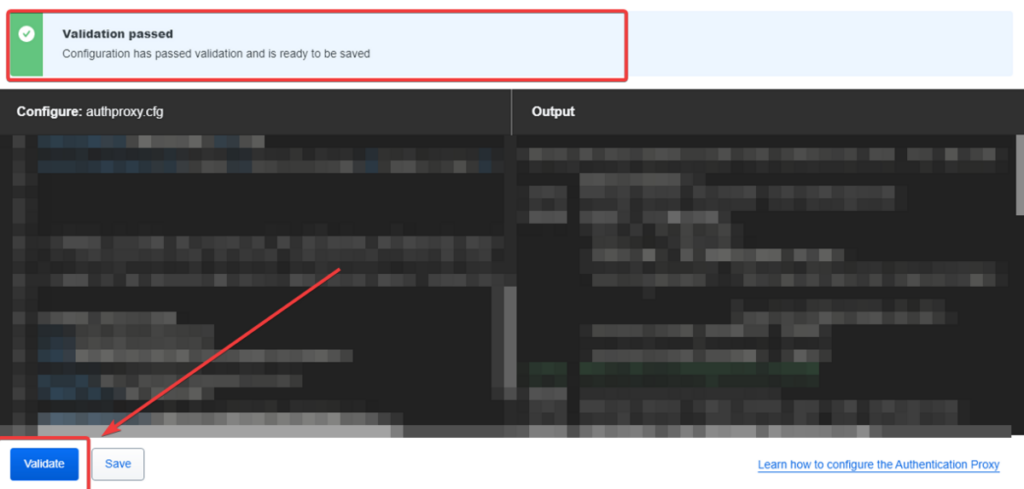
- Once you have modified the authproxy.cfg, click Validate in the bottom left. It should show Validation passed. If not, please review what you entered.
- Click the Save button in the bottom left
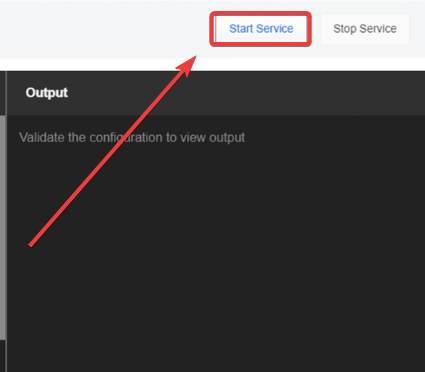
- Click Start Service in the top right if it isn’t already started once saving
SonicWALL Setup
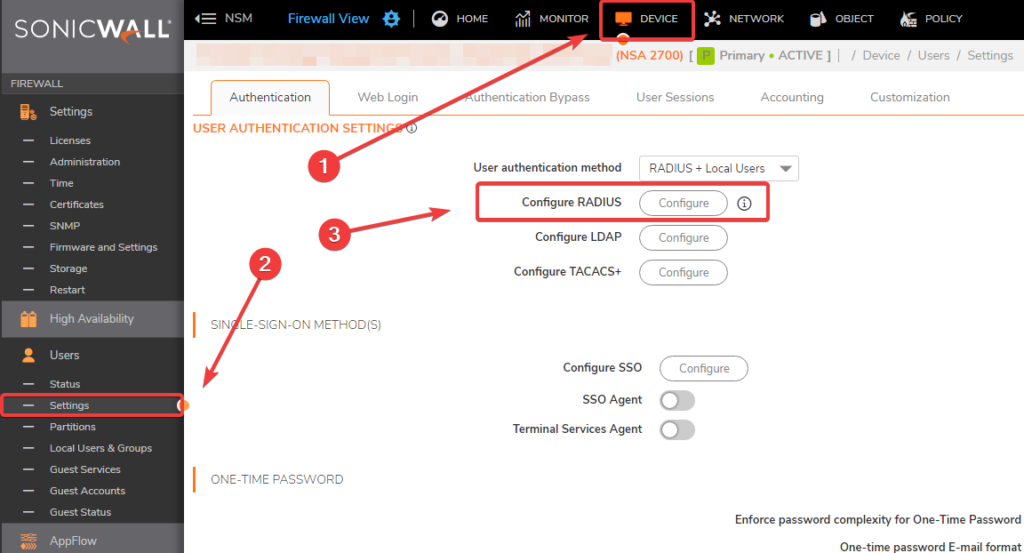
- Go to Device > Users > Settings and click on the Configure button next to Configure RADIUS in the User Authentication Settings section
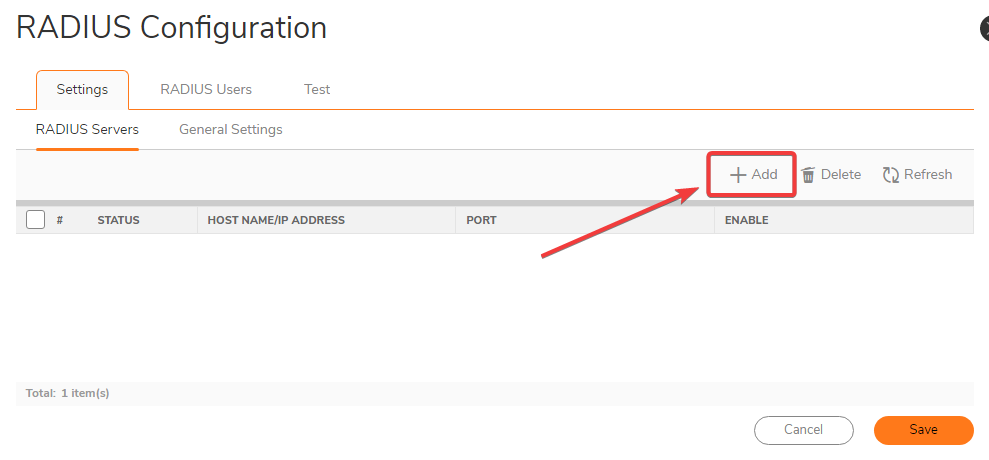
- Within the Settings tab under RADIUS Servers, add the Hostname/IP Address of the server that you setup the DUO Authentication proxy on
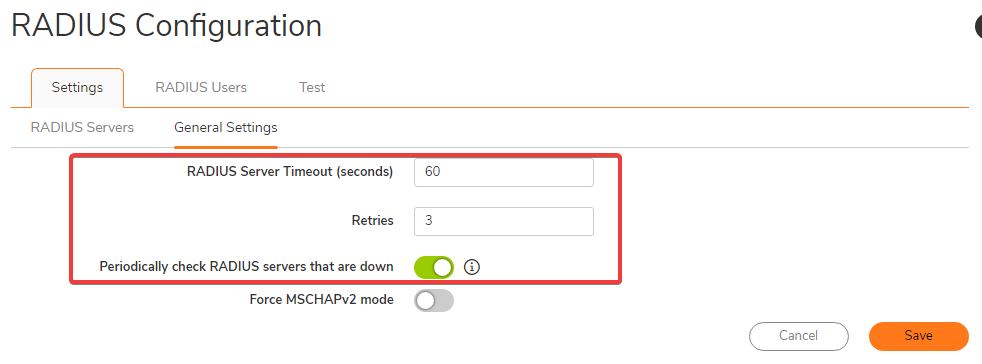
- Within the General Settings section use the following settings as recommended by DUO as well as checking Periodically check RADIUS servers that are downRADIUS Server Timeout (seconds) : 60
Retries: 3
- In the RADIUS Servers tab, hover over the RADIUS server you created and click the Edit Button
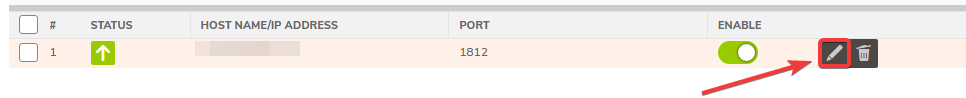
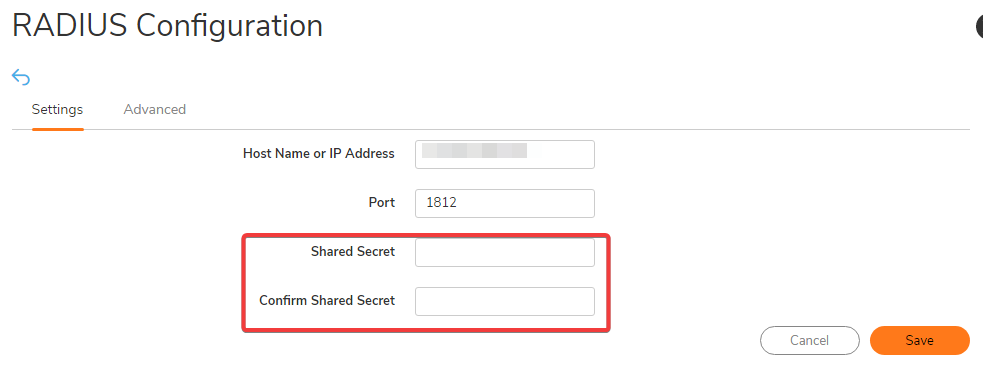
- Enter in the Shared Secret that was previously created from the DUO Authentication Step for use here
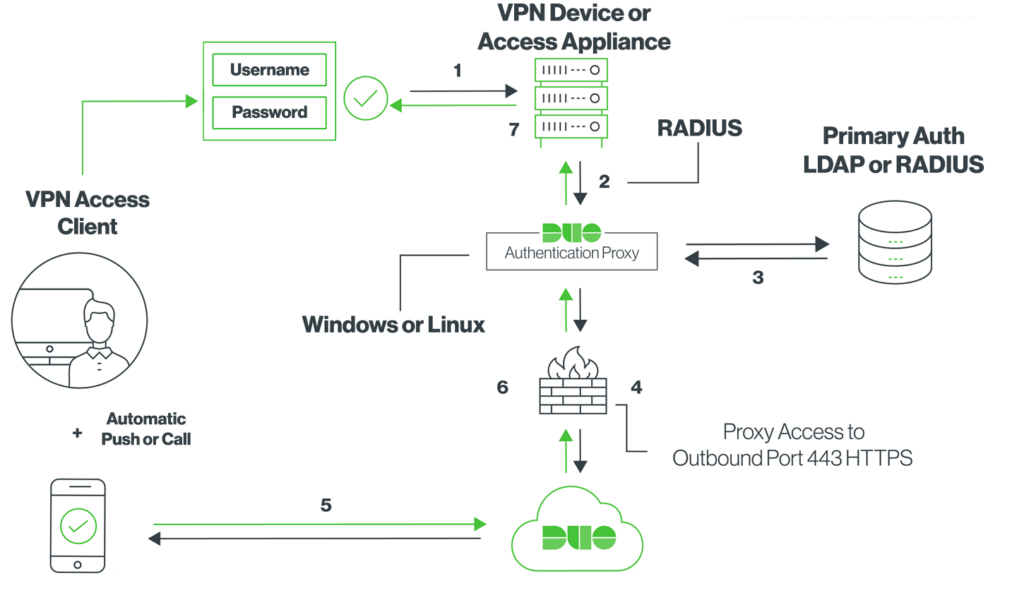
Configuration should be all done now and it should work once tested, please let me know if you have any questions. Below is a diagram on how specifically it works step by step.
Network Diagram
-
Primary authentication initiated by user logging into the NetExtender VPN
-
SonicWALL sends the authentication request to the Duo Security Authentication Proxy housed on the configured server
-
Primary authentication to Active Directory via LDAP using LDAP service account
-
Duo Authentication Proxy connection established to Duo Security over TCP port 443
-
Secondary authentication via Duo Security’s service
-
Duo Authentication Proxy on the configured server receives authentication response
-
SonicWALL receives authentication response, and NetExtender is given access